Update: CMMC v2.0 was announced in November 2021. This new version makes large-scale changes to the original model, aligning more closely with NIST SP 800-171 and removing third-party registration for some contractors. The article below relates to the outdated requirements of CMMC v.10. To learn more about the updated standard, please look at our article on CMMC v2.0.
The release of the newest cybersecurity compliance program, the Cybersecurity Maturity Model Certification (CMMC v. 1.0), provides new and updated guidance that helps companies work toward the same overarching goals stated in the NIST SP 800-171 standard – to protect CUI and improve security practices.
Despite encouragement by the DoD, less than 1% of Defense Industrial Base (DIB) companies have adopted all 110 controls in the NIST program. CMMC will combat the systemic non-compliance found across contractors and subcontractors working in the defense industry and provide scalability to make the program more accessible up and down the supply chain.
While both programs work toward improved cybersecurity function for any business, a close examination of the requirements highlights key differentiators that make the case for organizations to pursue the new requirements on top of or in tandem with NIST certification.
CMMC Certification Does Not Equal NIST Compliance, and Vice Versa
O that self-attesting to NIST compliance does not automatically qualify for CMMC certification, and vice versa. The NIST controls are required to comply with the DoD contractual requirements of DFARS 252.204-7012. They were added to the DFARS
CMMC Requires Third-Party Assessment
When working to comply to NIST 800-171, companies are given the luxury of self-attesting, claiming compliance or intent for compliance within a given time frame. This allowed for significant wiggle room as companies are able to continue providing products and services in continuance with the development of their security improvement initiatives.
Conversely, the required CMMC certification will be awarded only after a third-party assessment and audit of implementation of controls. A system Security Plan (SSP) and Plan of Action and Milestones (POA&M) must be fully completed prior to CMMC audit requests, ensuring that weaknesses are fully addressed and companies are prepared for wholly secure operation. On the other hand, NIST allows for SSP and POA&M actions to be in-progress as long as a target completion date is specified.
CMMC 3rd Party Assessment Organizations (C3PAOs) will be trained and tested on CMMC, submit to extensive background checks, and be licensed by the Accreditation Body (CMMC-AB).
CMMC is Required to Win Contracts
While DFARS compliance allows for attestation that NIST standards are being addressed, CMMC will serve as the gatekeeper when it 
The trickle-down is deep. Due to the vast number of suppliers with the ability to impact CUI, even small organizations that are seemingly less involved in the security of a project (like component manufacturers, IT managed services, and even janitorial services) will be held accountable to the appropriate CMMC certification level. When working toward CMMC certification, companies should examine their supply chain to determine CMMC-level requirements that must flow down to their suppliers.
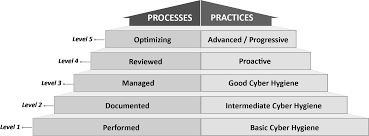
CMMC Offers Levels, Controls, and Scalability
Perhaps the most prominent and recognizable difference between the CMMC and NIST programs is their methods of structure. Where NIST provides controls at one basic level with supplemental enhancements for added protection, CMMC tiers specify truly definitive levels of compliance to which companies need to comply based on their products, services, and position in the defense industry.
From Level One, “Basic Cyber Hygiene,” to Five, “Advanced Security Operations,” CMMC provides a nuanced and specific set of requirements that is directly related to the sensitivity and quantity of CUI a company handles or processes.
All defense contractors must achieve at least Level One certification, and missing even one requirement of an intended level will result in failing certification. It’s a stringent and intentional method of protection that lays clear ground rules.
It’s also incredibly scalable. As the DoD works to build up cybersecurity maturity in small suppliers, the NIST requirements are pared down so that they are more applicable – via CMMC – to organizations who truly don’t need the same level of robust security protocols. Level One compliance includes just 17 controls, and Level Two is set at an easily manageable 72.
Equally, organizations working with extremely sensitive and highly protected information on a large scale can work toward Level Five certification, which takes the NIST requirements and amps them up include a total of 171 different controls, all aimed at ensuring the highest levels of cybersecurity practice and maturity. The more than 30 new practices added on top of NIST compliance factors are derived from a variety of programs (including NIST 800-171B (or NIST 800-172) and FAR clause 52.204-21) and practices from the NIST Cybersecurity Framework (CSF), CERT Resilience Management Model (CERT-RMM), and the Center for Internet Security (CIS).
Falling in the middle, CMMC Level 3 will likely become the industry norm, falling very close to basic requirements of NIST 800-171. This is where prior work toward NIST certification will prove to be extremely beneficial to early adopters, setting them up for quick success and a trouble-free CMMC audit.
CMMC Expands Domains, Process Maturity, and Cyber Threat Intelligence
NIST 800-171 focuses on 14 domains across cybersecurity, all aimed at controls and practice. CMMC adds three new domains, adding new focus on asset management, recovery, and situational awareness.
The result of these new domain additions to CMMC allows for organizations to focus on the continuous improvement of their cybersecurity operations.
Beginning at Level Two, CMMC works to assess not just the practices of an organization, but their growth and ability to institutionalize and mature their cybersecurity processes. It adds steps and future planning to the NIST 800-171 regulations, helping companies look far into the future. With the speed of cyber threats increasing daily, CMMC allows companie
Moving Forward with Expertise
The DoD aims to require CMMC by the fall of 2020 in several prime contracts that affect up to 1500 suppliers, giving companies an abbreviated timeline in which to become certified. Within 5 years, all DoD contracts will require CMMC certification and impact the nearly 350,000 organizations in the defense industrial base (DIB). Identifying current standings against NIST controls is a great place for companies to start as they prepare to tackle the CMMC certification process.
Partnering with security control experts, employing compliance tools, and meticulously organizing and tracking progress will be vital to meet the tight turnaround time. Additionally, careful budgetary planning will be critical to success.
From full-service providers to simple consultation, cybersecurity experts are prepared to help organizations through this tight timeframe. By examining NIST compliance, CMMC consulting professionals can help determine which CMMC levels are appropriate, pinpoint specific security control requirements, develop and launch implementation, and provide support through the audit. Through cloud-based software, the long-term maintenance of both CMMC and NIST 800-171 compliance can become routine.
The urgency of CMMC certification can feel heavy, especially for small businesses with limited budgets and lean workforces. But once it’s fully active, the risk of not being CMMC certified will result in loss of defense contracts. By combining the practices of NIST 800-171 and CMMC and working within the framework of the programs to increase cybersecurity process and practices, companies are set up for both immediate certification and continued growth that will position them for long-term success.
For information on how to start the process to be CMMC compliant and ready for CMMC certification, email info@thecoresolution.com or call 866.354.0300.