
Soon, all DoD contractors will need to meet these requirements to keep their contracts. Other government agencies are already considering CMMC as a security standard for contractors.
But these requirements won’t look the same for everyone. As a maturity model, CMMC comes in three different levels. These levels build on one another, adding more practices as they go. Your required level depends on the type of information you handle.
CMMC primarily deals with two types of government information: FCI and CUI. To understand CMMC and your cybersecurity responsibilities, you need to understand these two terms.
Want to learn more about securing FCI and CUI? Click here to watch a video.
What are CMMC’s 3 Primary Objectives?
CMMC has three primary objectives: to sustain and verify cybersecurity, to create a unified standard, and to protect sensitive defense-related information.
Cybersecurity can be thought of as information security. The goal of CMMC—and of all cybersecurity practices—is to keep important information out of the wrong hands.
CMMC exists to protect information that, if jeopardized or stolen by our nation’s adversaries, could be used for harm. This includes technical information, such as design drawings, and contract information, such as organizational charts. It’s anything that could give our nation’s adversaries a tactical advantage or lead to further breaches. When such information resides in secure government systems, it’s difficult to exfiltrate.

But as that information flows down to contractors and sub-contractors, the potential vulnerabilities grow exponentially.
Our nation’s adversaries have learned that it’s much easier to steal sensitive information from outside contractors with poor cybersecurity.
That’s why CMMC focuses on protecting information, whether that information resides on your network, a supplier’s network, or a customer’s network. The more sensitive that information, the higher the CMMC level required.
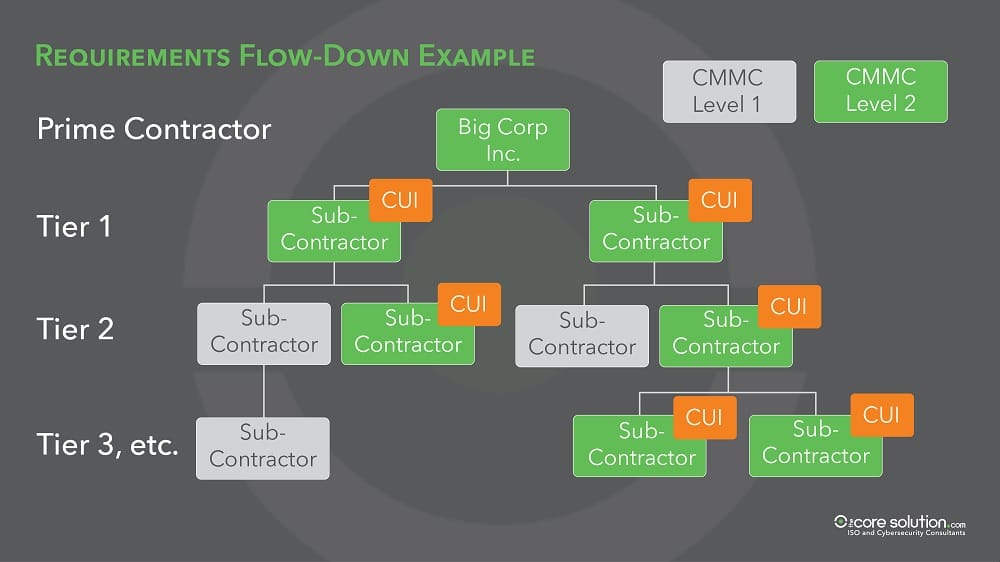
What is the Difference between FCI and CUI?
Let’s begin with the first type of protected information: Federal Contract Information, or FCI.
Definition of Federal Contract Information (FCI)
“Information, not intended for public release, that is provided or generated for the Government under a contract to deliver a product or service to the Government.”
– Official Government Definition of FCI
CMMC Level 1 exists to protect FCI. This is any non-public information exchanged with the government about a contract. This includes information exchanged during the proposal phase, the RFP phase, the award phase, or any information used to maintain that contract.
This does not include technical information, such as designs or drawings. That information takes you to another level of CMMC requirements. Instead, FCI comprises the day-to-day correspondence and documentation that comes with all government contracting. Every contractor in the Defense Industrial Base handles FCI.
Specific Examples of FCI Include:
-
Contract performance reports
-
Organizational or programmatic charts
-
Process documentation
-
Proposal responses
-
Past performance information
-
Contract information
-
Emails exchanged with the DoD or defense contractor

Because every DoD contract contains FCI, every contractor will require at least CMMC Level 1. The previous cybersecurity requirements of NIST SP 800-171 did not cover this type of information, so many contractors will now need to think about cybersecurity for the first time.
Definition of Controlled Unclassified Information (CUI)
“CUI is information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.”
– Official Government Definition of CUI
Specific examples of CUI include:
-
Information Systems Vulnerability Information
-
Personally Identifiable Information (PII) (Could be your employees, government employees, or even employees of a third party)
-
Research and engineering data
-
Engineering drawings
-
Specifications
-
Standards
-
Process sheets
-
Manuals
-
Technical reports
-
Technical orders
-
Catalog-item identifications
-
Data sets
-
Studies and analysis
-
Executable code and source code
You can access the full CUI Registry at www.archives.gov/cui


In the future, CUI will be clearly labeled on government contracts. But at the moment, it’s not always clear whether your contract contains CUI. Sometimes it’s obvious, as with technical drawings or source code. Other times, it’s not so obvious.
As a general rule of thumb: If it describes the technical aspects of a product or system, it’s CUI.
The safest approach? Treat everything in your contract as if it’s CUI. It’s better to be prepared and safe than to risk losing a lucrative government contract, or worse, to risk an actual security breach.
How Core Business Solutions Can Help
At Core Business Solutions, we specialize in helping American small businesses achieve cybersecurity. As a Registered Provider Organization with the CMMC Accreditation Board, we are officially recognized as a trusted provider of CMMC consulting and solutions.
We’re real people with a story like yours, and we have a team of InfoSec consultants ready to help. Our security solutions are constantly evolving to meet government requirements and the ever-changing cyber-threat landscape.
We take on the complicated parts of certification so that you can focus on your business. Learn more about our CMMC consulting programs or get a free quote today.
Core Business Solutions, established in 2000, is a Registered Practitioner Organization through the Cyber AB and has been providing consulting and technical solutions for NIST/CMMC for over 5 years. Rick Krick is the Director of Security Solutions for Core Business Solutions and directs our Cybersecurity Services solutions including CMMC. Rick has over 25 years of experience in Management System implementations, software development, IT services, and certifications.




